Featured
Table of Contents
- – Ipsec Vs. Openvpn: What's The Difference? - Iot...
- – Guide To Ipsec Vpns - Nist Technical Series Pu...
- – How Does Ipsec Work With Ikev2 And Establish A...
- – What Is Internet Protocol Security (Ipsec)?
- – Ipsec Vpn
- – Transport Mode - An Overview
- – What Is Ipsec And How It Works
- – What Is Ipsec?
- – Ipsec Vpn Overview
- – Ipsec Vpn
Ipsec Vs. Openvpn: What's The Difference? - Iot Glossary
IPsec (Internet Procedure Security) is a structure that helps us to secure IP traffic on the network layer. IPsec can secure our traffic with the following functions:: by securing our data, nobody except the sender and receiver will be able to read our data.
By calculating a hash worth, the sender and receiver will be able to inspect if modifications have actually been made to the packet.: the sender and receiver will confirm each other to make certain that we are actually talking with the gadget we intend to.: even if a packet is encrypted and verified, an opponent could try to capture these packets and send them again.
Guide To Ipsec Vpns - Nist Technical Series Publications
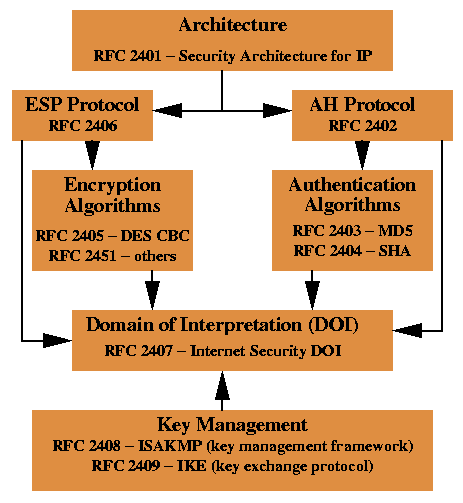
As a framework, IPsec utilizes a variety of protocols to implement the features I described above. Here's an introduction: Don't fret about all the boxes you see in the photo above, we will cover each of those. To provide you an example, for encryption we can select if we wish to use DES, 3DES or AES.
In this lesson I will start with an overview and after that we will take a more detailed look at each of the parts. Before we can protect any IP packages, we require 2 IPsec peers that construct the IPsec tunnel. To establish an IPsec tunnel, we use a procedure called.
How Does Ipsec Work With Ikev2 And Establish A Secure ...
In this phase, an session is established. This is likewise called the or tunnel. The collection of specifications that the 2 devices will utilize is called a. Here's an example of 2 routers that have developed the IKE stage 1 tunnel: The IKE stage 1 tunnel is only used for.
Here's an image of our 2 routers that completed IKE stage 2: As soon as IKE stage 2 is finished, we have an IKE stage 2 tunnel (or IPsec tunnel) that we can use to secure our user data. This user information will be sent through the IKE stage 2 tunnel: IKE develops the tunnels for us however it does not validate or secure user data.
What Is Internet Protocol Security (Ipsec)?


I will explain these two modes in information later in this lesson. The whole procedure of IPsec consists of five actions:: something has to set off the development of our tunnels. When you configure IPsec on a router, you utilize an access-list to inform the router what data to safeguard.
Everything I explain listed below uses to IKEv1. The main function of IKE stage 1 is to establish a safe and secure tunnel that we can utilize for IKE stage 2. We can break down stage 1 in 3 easy actions: The peer that has traffic that ought to be protected will initiate the IKE stage 1 negotiation.
Ipsec Vpn
: each peer needs to prove who he is. Two typically used choices are a pre-shared secret or digital certificates.: the DH group determines the strength of the key that is used in the key exchange procedure. The greater group numbers are more safe however take longer to calculate.
The last action is that the 2 peers will confirm each other using the authentication method that they agreed upon on in the negotiation. When the authentication achieves success, we have actually finished IKE phase 1. Completion outcome is a IKE stage 1 tunnel (aka ISAKMP tunnel) which is bidirectional.
Transport Mode - An Overview
Above you can see that the initiator uses IP address 192. IKE uses for this. In the output above you can see an initiator, this is an unique worth that identifies this security association.
The domain of analysis is IPsec and this is the very first proposition. In the you can find the qualities that we want to use for this security association.
What Is Ipsec And How It Works
Since our peers concur on the security association to utilize, the initiator will start the Diffie Hellman key exchange. In the output above you can see the payload for the essential exchange and the nonce. The responder will likewise send his/her Diffie Hellman nonces to the initiator, our two peers can now calculate the Diffie Hellman shared key.
These 2 are used for recognition and authentication of each peer. IKEv1 primary mode has now finished and we can continue with IKE phase 2.
What Is Ipsec?
1) to the responder (192. 168.12. 2). You can see the change payload with the security association attributes, DH nonces and the recognition (in clear text) in this single message. The responder now has everything in needs to generate the DH shared essential and sends out some nonces to the initiator so that it can also compute the DH shared secret.
Both peers have everything they require, the last message from the initiator is a hash that is used for authentication. Our IKE phase 1 tunnel is now up and running and we are all set to continue with IKE stage 2. The IKE stage 2 tunnel (IPsec tunnel) will be actually used to safeguard user information.
Ipsec Vpn Overview
It protects the IP packet by determining a hash worth over nearly all fields in the IP header. The fields it excludes are the ones that can be altered in transit (TTL and header checksum). Let's start with transportation mode Transportation mode is easy, it simply includes an AH header after the IP header.
With tunnel mode we add a brand-new IP header on top of the initial IP packet. This might be helpful when you are utilizing personal IP addresses and you require to tunnel your traffic over the Internet.
Ipsec Vpn
It likewise provides authentication however unlike AH, it's not for the whole IP packet. Here's what it looks like in wireshark: Above you can see the original IP packet and that we are using ESP.
The original IP header is now likewise encrypted. Here's what it appears like in wireshark: The output of the capture is above resembles what you have actually seen in transport mode. The only difference is that this is a new IP header, you do not get to see the initial IP header.
Table of Contents
- – Ipsec Vs. Openvpn: What's The Difference? - Iot...
- – Guide To Ipsec Vpns - Nist Technical Series Pu...
- – How Does Ipsec Work With Ikev2 And Establish A...
- – What Is Internet Protocol Security (Ipsec)?
- – Ipsec Vpn
- – Transport Mode - An Overview
- – What Is Ipsec And How It Works
- – What Is Ipsec?
- – Ipsec Vpn Overview
- – Ipsec Vpn
Latest Posts
Best Vpn Services Of 2023 - Four Industry Leaders To ...
The 6 Best Vpn Stocks To Buy Right Now For August 2023
Best Vpn For Mobile 2023: Staying Safe On Android And Ios
More
Latest Posts
Best Vpn Services Of 2023 - Four Industry Leaders To ...
The 6 Best Vpn Stocks To Buy Right Now For August 2023
Best Vpn For Mobile 2023: Staying Safe On Android And Ios